Enhance your vulnerability management with dynamic Penetration Testing as a Service (PTaaS)
Mitigate risks before they happen with our innovative PTaaS solution. We combine the best of innovative technology with the irreplaceable insights of seasoned professionals to deliver tailored, effective cybersecurity services. We empower organizations to identify vulnerabilities, mitigate risks, and ensure robust protection against evolving cyber threats.
Stop threats in their tracks.
Discover PTaaS in 60 seconds!
Join 1,000+ leading companies who trust Rootshell Security




Dynamic penetration testing to secure your most critical assets

Personalized penetration testing as a service (PTaaS) packages
Your tailored PTaaS security package is modular, from penetration testing, MVS (managed vulnerability scanning), ASM (attack surface management) and red team assessments to include the elements that satisfy your requirements. Your PTaaS results and data are delivered through The Rootshell Platform, giving you program oversight and vulnerability remediation management tools as standard. Rootshell PTaaS is offered as a 12-month contract.

Attack surface management solutions
Access a fully managed vulnerability scanning service, including manual reviews and expert guidance from your dedicated consultant. We’ll regularly scan your internal and external infrastructure, networks and applications and make all results available directly in our platform.
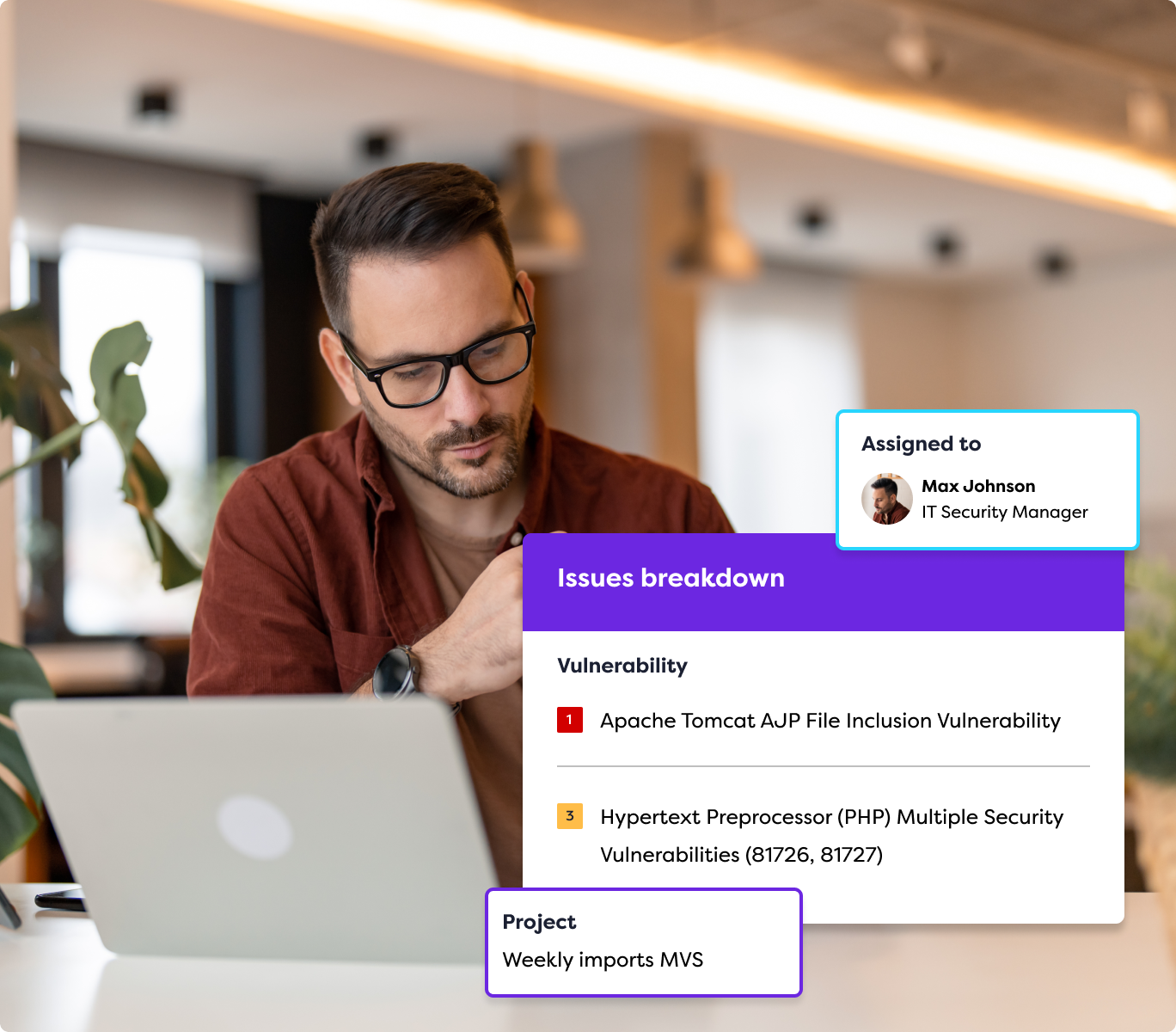
A centralized dashboard for improved visibility and control
No static, out-of-date PDFs or stuffy spreadsheets to trawl through here. You’ll get a dynamic, single window into your penetration testing results, vulnerability scanning and exploit intelligence. The Rootshell Security platform provides a holistic view of your organization’s vulnerabilities so you know what needs fixing first.

Ongoing support for cyber resilience
As the threat landscape changes, so will the suppliers you work with. Whether you’re using our PTaaS services, or consolidating data from providers across your supply chain, our platform acts as a vendor-neutral, single source of truth for consolidating your cyber security data over time.
Choose from an array of penetration testing and cyber security services to suit your business
Gain peace of mind with comprehensive vulnerability assessments.
Resolve vulnerability exploits before they become bigger issues
Dynamic penetration testing to secure your most critical assets
exploitable issues
active exploit issues

👋Goodbye static spreadsheets, hello dynamic hub with real-time insights
Find and fix vulnerabilities with a modern vulnerability management platform that combines ongoing managed scanning with AI-led Active Exploit intelligence. Store data from any penetration testing vendor or security service provider in one centralized hub for continuous protection.
See the platform in action
Watch us revolutionize your security.
You won’t want to miss this!
Active exploit detection
Identify and mitigate threats in real-time.
Automation center
Automate routine security tasks for increased efficiency.
Remediate & collaborate
Work seamlessly with your team to resolve vulnerabilities.
Integrations
Connect with your marketing-leading tools for a unified security approach.
Recognized industry leader in penetration testing as a service (PTaaS)



Empower your business with cutting edge security
Choosing Rootshell Security means partnering with a team dedicated to protecting your business. Our expert guidance ensures your security solutions are set up correctly and maintained for optimal performance. With detailed threat insights and AI-powered intelligence, we help you stay ahead of potential threats and enhance your security posture.
Insight into an ever-evolving threat landscape
Gain full security visibility with in-depth threat insights. Our AI analysis and threat intelligence team provide actionable intelligence to protect you in real-time.
Dedicated support from an expert team
Your dedicated security consultant guides you from setup to maintenance, ensuring your solutions are optimized and effective.
Make traditional processes redundant
Our platform provides a single source of truth with easily exportable, drillable data to give back time and resources to your in-house team.
Quick issue resolution with fast remediation
Accelerate the remediation process from start to finish with automated prioritisation and vulnerability prioritisation.
Uncover hidden threats in vulnerability data
Connect the dots with a centralized platform to discover and address hidden exploits within your existing vulnerability information.
Market-leading features
From Active Exploit Detection to Enterprise-Grade Automation abilities, it’s easy to see why leading organizations choose Rootshell Platform.
Unlock the full potential of your security strategy
Hear why the world’s top companies place their trust in us

Rootshell Security goes beyond being a service provider; they are a vital component of our cybersecurity strategy. Their expertise, coupled with the game-changing Rootshell Platform, has significantly strengthened our cybersecurity management, enabling us to adapt swiftly and bolster our overall security posture.
CISO | Trainline
Read Trainline's success story
Rootshell’s services along side the remediation management platform, has provided reassurance and improved our efficiency around our pen testing programme.
Rex Slater, CISO | Edenred
Read Edenred's success story
The Rootshell Platform gives me the visibility to easily understand issues, approve projects, and collaborate with colleagues so that our remediation process is as streamlined as possible. The platform is incredibly intuitive for non-technical leaders like me. The tooltips and training make it really easy to get the most out of the platform.
Stephen Shackell, Director of Intelligence and Risk | Zinc
Read Zinc's success story

Access all the resources you need to help you protect and secure your business
Explore our resources to learn how Rootshell Security can help strengthen your cybersecurity posture, identify vulnerabilities, and protect your organization from threats.
Looking for help from an expert? Book A Demo
Frequently asked questions & answers
Can’t find the answer to your question?
You can always Contact Our Team of experts for a chat!
What is Penetration Testing as a Service (PTaaS)?
Penetration testing as a service (PTaaS) is an in-depth ethical cyber security assessment. It’s a hybrid solution that combines automated and human testing and reporting to safely identify and exploit vulnerabilities to proactively safeguard against cyber crime.
What types of penetration tests can I request through the platform?
From phishing to firewalls, we’ll create a bespoke pentesting package based on your business’s requirements. We can even offer red team as a service to simulate a real-world cyber-attack.
How does Rootshell Security’s PTaaS platform work with PTaaS?
Our vulnerability management platform provides a dynamic view of your penetration test results for a better way to track and remediate vulnerabilities. As a vendor-neutral platform, you can consolidate data from your various security vendors for single-pane visibility of the attack surface.
How often should I conduct penetration tests using PTaaS?
Penetration testing should be performed on a regular basis, with many of our clients running tests continuously across their attack surface. We recommend this, through a mixture of testing, scanning and continuous enrichment. If you are not sure what would be best for your business, or where to start, please get in touch and one of our experts would be happy to advise.
Why choose Rootshell Security?
We’re proud to be a trusted provider of PTaaS for some of the UK’s largest organizations. We combine the best of innovative technology with the irreplaceable insights of seasoned professionals to offer bespoke, effective cybersecurity solutions through our platform, seamlessly integrating traditional penetration testing into your security programme.