Active exploit detection
Stop threats in their tracks with active exploit detection & protection
Our AI-powered exploit detection continuously scans for active threats, sending instant notifications when vulnerabilities are detected. It provides detailed context beyond CVSS scores, helping you prioritize and respond to threats more effectively.

An easier way to prioritize for exploit
protection
The Rootshell Platform uses AI to proactively gather the latest exploit intelligence and apply it to your consolidated vulnerability data to uncover and alert you to hidden risks in your estate.
AI threat finder
The Rootshell Platform continuously scans your technology estate for any issues that are being actively exploited by threat actors in the wild.
Immediate exploit detection notifications
If the Rootshell Platform detects any vulnerabilities across your network, you’ll receive an instant, real-time alert to facilitate swift remediation.
AI-powered insights into the threat landscape
Velma, our AI threat finder scans thousands of information sources to discover the issues that are currently being used by threat actors to launch attacks.
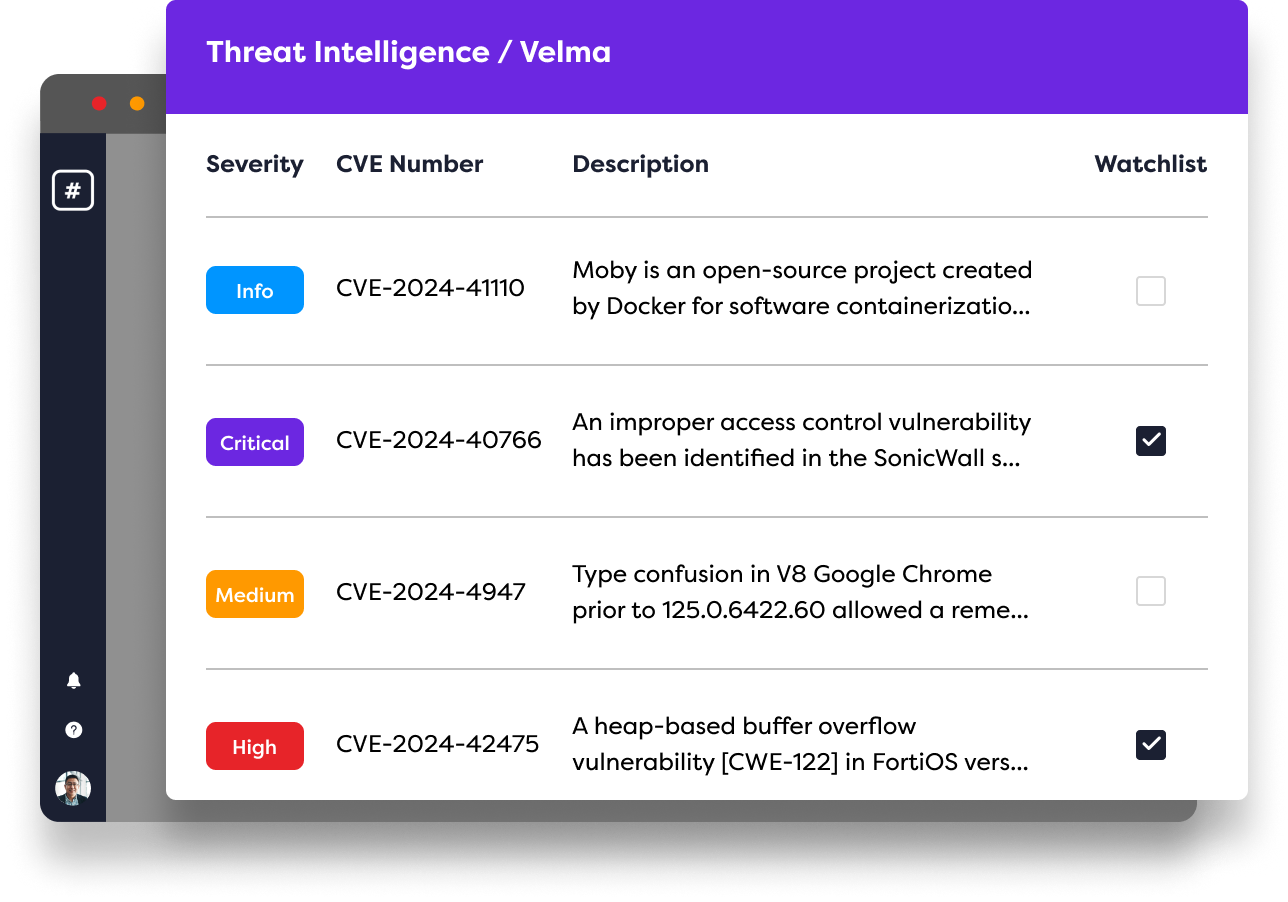
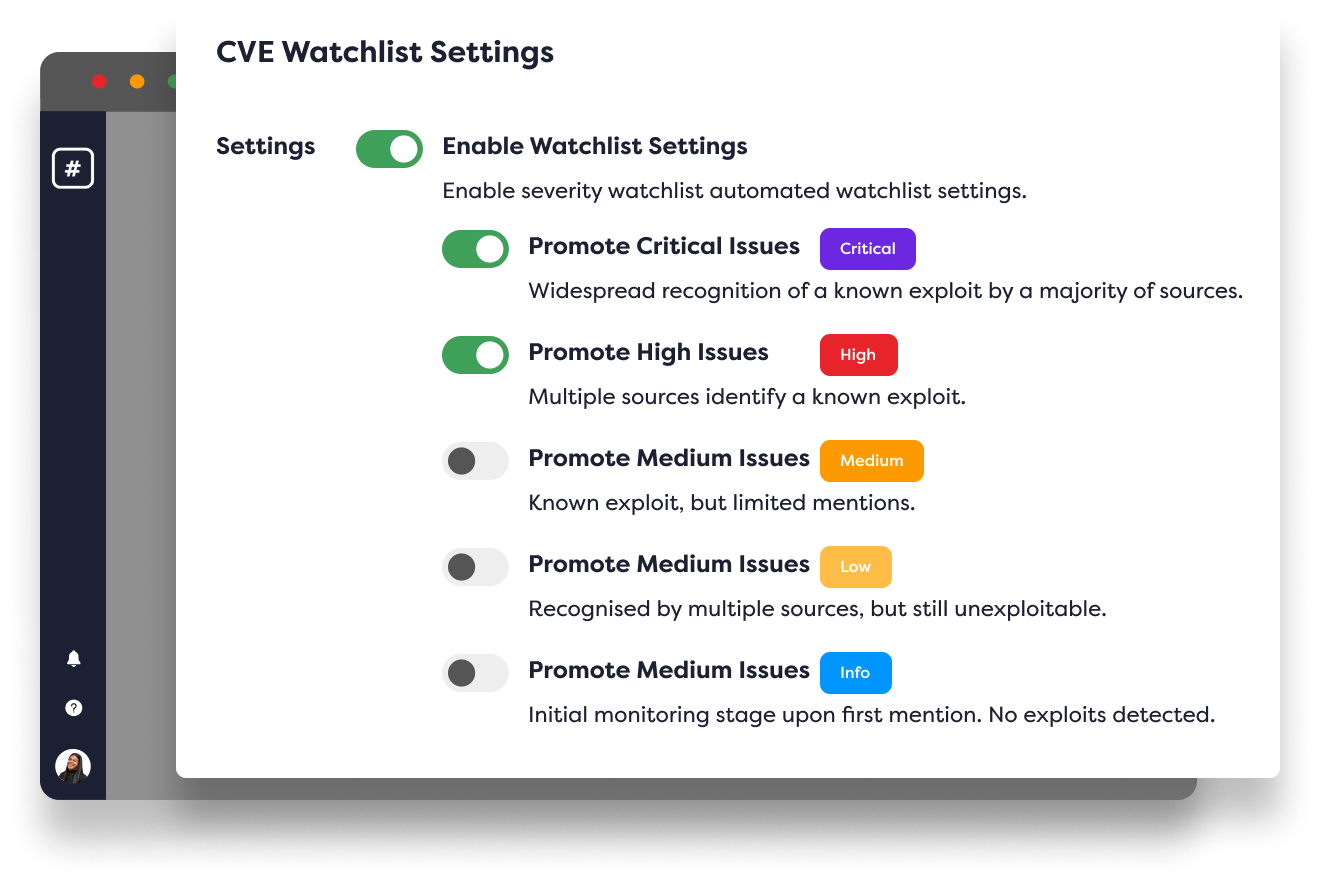
Instant active exploit detection alerts
Rootshell’s active exploit detection overhauls point-in-time reporting and provides teams with powerful, continuous surveillance.
Cut through the noise of vulnerability data
The platform provides the context needed to cut through the noise of vulnerability data, pinpointing which issues are truly most vulnerable to you.
Made for modern IT teams
Automate remediation workflows in minutes and empower your IT team to implement the most effective exploit protection prioritization as soon as possible.
Backed by trusted intelligence sources
Our active exploit detection scans the leading sources of exploit information to keep your organization’s defenses ahead of the curve.
Reputable information sources
We’ve integrated our exploit detection with:
- Cybersecurity and Infrastructure Security
- Agency (CISA)
- Zero Day Initiative
- Exploit DB
- NVD
Cutting-edge technology
For even greater context of the threat landscape, our own AI threat finder, Velma, scans thousands of information sources to uncover the latest exploits.

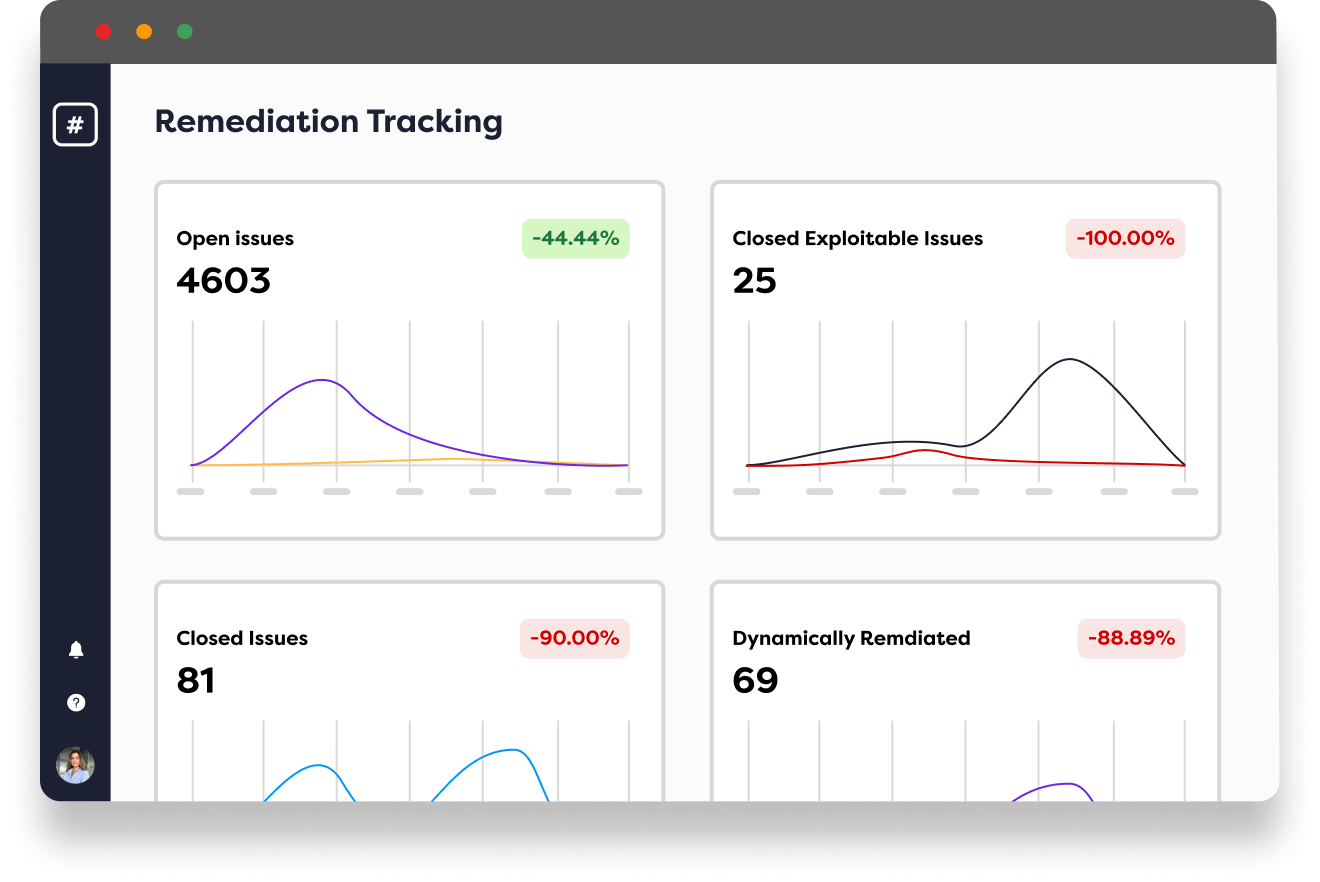
Track & manage exploit remediation
The Rootshell Platform supports your team beyond active exploit detection.
Integrates with your chosen project management tools
The Rootshell Platform integrates with leading project management tools, so you’ll be able to assign team members to patch and fix vulnerabilities.
Track remediation progress all in one place
View your active exploits at a glance with the Rootshell Platform’s dashboard view, or drill down for more detail.
Here’s why you should implement active
exploit detection
Reduce cyber-attack risk
By identifying vulnerabilities as they appear, organizations can reduce the risk and potential costs of cyber-attacks.
Improve security posture
Organizations can assess and improve their security posture by identifying and tracking vulnerabilities over time.
Comply with regulations
Regular vulnerability scanning is important for ensuring compliance with industry regulations.
Prevent data breaches
Vulnerability management can prevent data breaches and other incidents that can damage a company's reputation and bottom line.
Save time for IT staff
Automated technologies provide IT security teams with threat data and risk priority scores, allowing them to spend more time closing security gaps.
Maintain visibility
Continuous vulnerability management is needed to maintain visibility in dynamic environments and changing threat landscapes.
Hear why the world’s top companies place
their trust in us
Rootshell Security goes beyond being a service provider; they are a vital component of our cybersecurity strategy. Their expertise, coupled with the game-changing Rootshell Platform, has significantly strengthened our cybersecurity management, enabling us to adapt swiftly and bolster our overall security posture.
Munawar Valiji, CISO | Trainline
Read Trainline's success story
The Rootshell Platform gives me the visibility to easily understand issues, approve projects, and collaborate with colleagues so that our remediation process is as streamlined as possible. The platform is incredibly intuitive for non-technical leaders like me. The tooltips and training make it really easy to get the most out of the platform.
Stephen Shackell, Director of Intelligence and Risk | Zinc
Read Zinc's success story

Frequently asked questions & answers
Can’t find the answer to your question?
You can always Contact Our Team of experts for a chat!
What is active exploit detection?
Active exploit detection ensures continuous vulnerability scanning and intrusion detection to instantly identify and send notifications when an attacker is attempting to exploit weaknesses.
How does the Rootshell Platform use AI for active exploit detection?
That’s where Velma, our AI threat finder comes in! Velma scours thousands of information sources to keep up to date with the latest vulnerabilities being exploited by threat actors. You’ll then get instant notifications of exploitable weaknesses to remediate. You can find Velma’s latest findings over in our Exploit Center.
Does the Rootshell Platform detect vulnerabilities in real-time?
Yes. Our AI-powered exploit protection tool continuously scans for possible threats across your attack surface and will send you an instant notification if a vulnerability is detected.
Can I see your active exploit detection in action?
Of course! Here’s everything you need to know about The Rootshell Platform. Want to see it in action? Book a free, no-obligation demo with the team.
How can exploit detection help mitigate against attacks?
Rootshell provides comprehensive support for users, including detailed documentation, customer service, and expert guidance to help you get the most out of the Automation Center. Whether you're setting up your first automation or optimizing existing processes, we're here to assist you.
