Penetration Testing Cloud Services
Identify and remediate critical vulnerabilities in your cloud services with penetration testing cloud services.

Trusted by companies of all shapes and sizes
What is cloud penetration testing?
Cloud penetration testing services assess an organization’s cloud services for security weaknesses. The aim is to identify vulnerabilities before they can be exploited; vulnerabilities that could otherwise lead to security breaches.
Rootshell Security’s Cloud Penetration Testing services investigate the configurations of Amazon Web Services (AWS) and Microsoft Azure environments against best practice standards. Using the same techniques as real-world threat actors, we then safely attempt to exploit identified vulnerabilities to confirm whether they could lead to a breach.
Our CREST-certified penetration testers provide expert guidance throughout, so you can remediate issues as quickly and effectively as possible to keep your organization secure.
Why should your organization use penetration testing for cloud services?
Uncover critical vulnerabilities
As the risk of cyber attacks continues to increase, it’s crucial you have complete visibility of your organization’s vulnerabilities. Our penetration testing services will identify any vulnerabilities within your cloud environments, from low to high risk, so you can take action.
Effectively remediate risk
Penetration tests provide you with the data you need to manage and resolve vulnerabilities. Our penetration testers offer expert support so you can remediate as quickly and effectively as possible.
Fortify your security posture
If left unmaintained, cloud services can provide convenient entry points for threat actors to breach your organization and steal sensitive data. Conducting penetration testing for your cloud services will provide your organization with critical protection.
View your cloud penetration testing results alongside your other vulnerability data
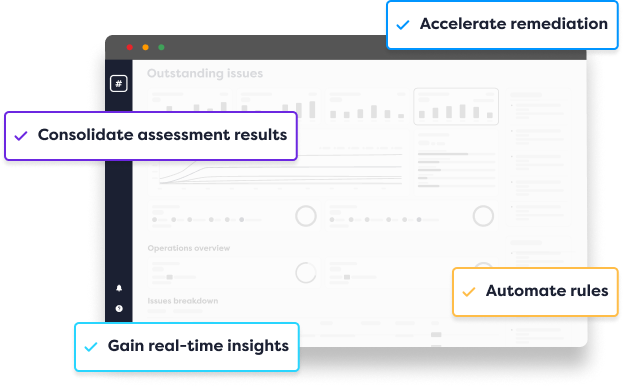
The Rootshell Platform is a vendor-agnostic vulnerability management solution that puts you at the centre of your IT security ecosystem. Consolidate assessment results, accelerate remediation from start to finish, and gain real-time insight into your ever-changing threat landscape.
Recognized industry leader in penetration testing as a service (PTaaS)
AWS cloud penetration testing
We can review the configuration of your AWS environment against best practice standards to help you identify and resolve vulnerabilities that could lead to an attack.
Build your package:
- Lambda
- Cloudformation
- Cloud trail
- Cloud watch
- Guard duty
- Directconnect
- EC2
- EFS
- Macie
- RDS
- S3
- VPC
Plus receive your results an data through The Rootshell Platform .
Azure cloud penetration testing
Our Azure Cloud Penetration Testing service assesses your Azure configuration against best practice standards. We can help you identify and resolve any issues within your cloud environment that could be exploited.
Build your package:
- Azure Functions
- Azure Resource Manager
- Azure Monitor
- ExpressRoute
- Azure Virtual Machines
- Azure File Storage
- Azure Cache
- Azure Databricks
- Azure Active Directory
- SQL Database, MySQL, and PostgreSQL
- Azure DNS
- Virtual Network
Plus receive your results an data through The Rootshell Platform .
Ready to get started?
Discover your needs
Dive into a personalized demo
Seamless onboarding
Why Rootshell’s security testing for cloud services?
We’re proud to provide penetration testing services for some of the UK’s leading organizations.
CREST-certified pen testing
CREST is an internationally recognised accreditation for penetration testing services. Our CREST-certified testers carry out your penetration testing services to the highest technical and ethical standards.
Quality assured
We deliver our penetration testing services to industry standards, such as Open Web Application Security Project (OWASP) guidelines, the National Institute for Standards and Technology (NIST), and the Penetration Testing Execution Standard (PTES).
Expert advice and support
Following your penetration test, our CREST-certified testers provide you with expert guidance and support. You will receive clear reports and advice, along with step-by-step instructions, ensuring you know exactly how to remediate and reduce risk.
Don’t just take our word for it, hear what our customers think
Frequently asked questions about red team assessments
Can’t find the answer to your question?
You can always Contact Our Team of experts for a chat!
What is pentesting for cloud services?
A penetration test simulates a real-world attack on your organisation’s cloud service. This enables you to identify any weaknesses or vulnerabilities so you can improve your defences against a real attack.
Does AWS allow penetration testing?
Yes – we can perform penetration testing on your AWS environment.
Which cloud providers do you offer penetration testing for?
Firstly, our CREST-certified testers conduct a manual review of the configuration of your cloud services. They carry out an exhaustive assessment of all the services that may be in use within your cloud environment, looking for any vulnerabilities.
Our testers will then use a combination of automated and manual techniques to attempt to safely exploit any identified vulnerabilities to determine whether they could enable a cyber attack. You will receive expert remediation guidance that ensures any issues are resolved quickly and effectively.
Our testers will also identify and analyse API calls in web applications to ensure that no sensitive data is being exposed.
How is cloud penetration testing carried out?
We offer a range of penetration testing services. Our security consultants can help advise which types of pen testing services your organisation needs.
Our penetration testing services include: Infrastructure Security Testing, Web Application Services Penetration Testing, Vulnerability Assessments, Firewall Audits, Phishing Simulation Assessments, Social Engineering Assessments, Wireless Security Assessments, Operating System Build Reviews, Hardware Device Security Reviews, VOIP Security Testing, SCADA Security Testing, OWASP Mobile Application Testing, and Simulated Attack Assessments.
How often should penetration testing for cloud services be carried out?
If unmaintained, cloud computing can leave your organisation vulnerable to cyber attacks. We recommend conducting a pen test any time you make significant configuration changes to the configuration your cloud services. Our team can advise the best solution for your organisation.
What penetration testing tools do you use?
Our testers use a combination of automated and manual techniques, which replicate the latest methods used by real-world threat actors.
What's the difference between a pentest and vulnerability scanning?
A penetration test simulates a real-world attack on your organisation’s network, applications, and systems to identify any weaknesses. A pen test is conducted by skilled consultants, who use the same techniques as real-word hackers; you can think of it as ‘ethical hacking’. On the other hand, vulnerability scanning is carried out using automated tools and solely focuses on identifying vulnerabilities within software. Find out more about vulnerability and penetration testing services.
What are continuous penetration testing services?
Rootshell Security’s Continuous Testing services help your organisation maintain and improve its security posture year-round. Our Continuous Testing services provide your organisation with an ongoing, real-time, and holistic security strategy, offering greater protection against cyber threats. Find out more about Continuous Penetration Testing.
What are the types of penetration testing?
We offer a range of penetration testing services. Our security consultants can help advise which types of pen testing services your organisation needs.
- Infrastructure Security Testing
- Web Application Services Penetration Testing
- Firewall Audits
- Phishing Simulation Assessments
- Physical Security Assessments
- Social Engineering Assessments
- Wireless Security Assessments
- Operating System Build Review
- Hardware Device Security Reviews
- VOIP Security Testing
- SCADA Security Testing
- OWASP Mobile Application Testing
- Simulated Attack Assessments

