Our Team have discovered a Remote Heap Corruption Bug within miniDLNA and Develop Proof of Concept Exploit
The Rootshell Security team have discovered a bug within miniDLNA; an open-source server software for exchanging media files, such as videos, between devices on a network.
The team identified that a remotely exploitable heap corruption issue exists within the miniDLNA software. Heap corruption occurs when memory allocation for data is handled incorrectly.
The bug is triggered when Universal Plug and Play (UPnP), a set of networking protocols that enable devices to exchange data, attempts to process requests for data transfer.
The root cause of the issue is due to miniDLNA inadvertently allowing a remote attacker to manipulate the length of data ‘chunks’; this is a method for transferring data (also known as ‘chunked transfer encoding’). An attacker could specify a large, and therefore negative, length for a chunk, which leads to memory corruption (due to an ‘out–of–bounds’ error in calls to the memory copy functions ‘memcpy’ and ‘memmove’).
As well as memory corruption, the bug could be exploited to cause an infinite loop. Both would result in a denial–of–service (DoS) attack.
Rootshell’s Head of Research and Development, Dr Neil Kettle, led the research. Below, he demonstrates how the issue can be found in the software’s ‘upnphttp.c’ file:
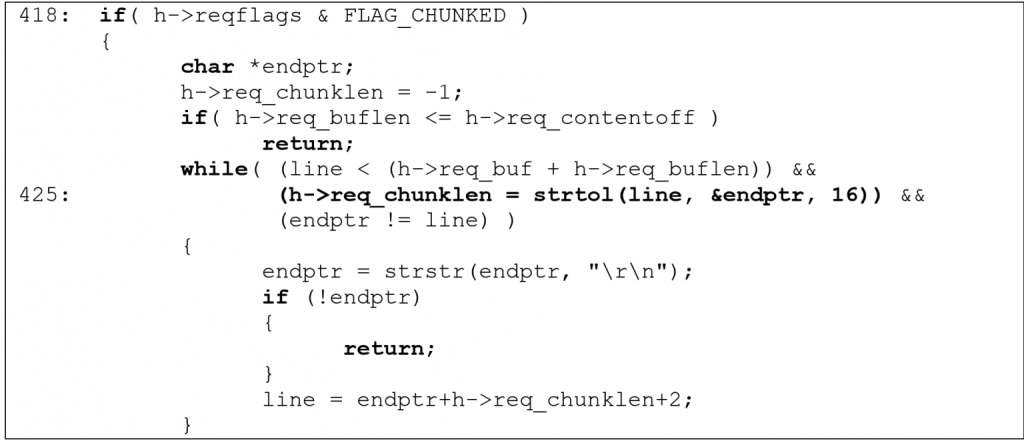
miniDLNA’s code fails to validate the return value of ‘strtol’. Therefore, the remainder of the code can be made to utilise negative values for ‘h->req_chunklen‘.
An example exploitation attempt is given below:
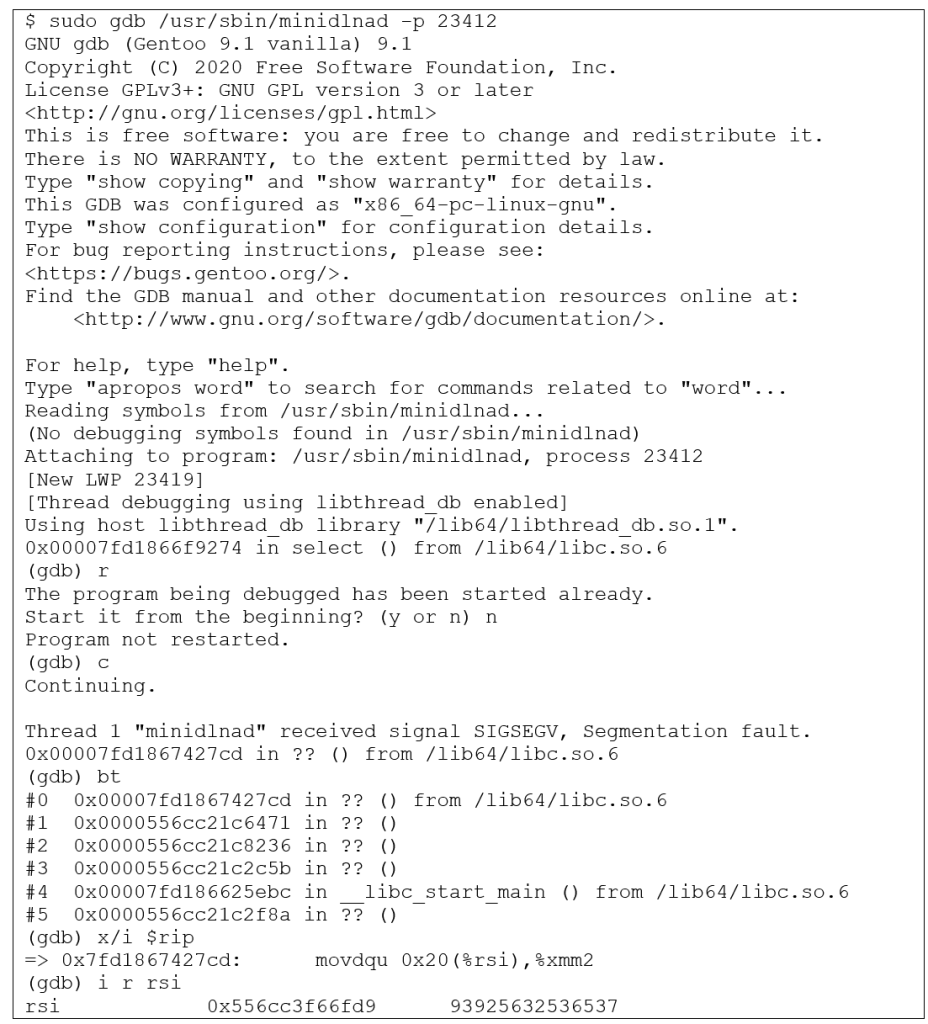
Following the discovery of the bug, the Rootshell team have developed a proof of concept for an exploit, which uses memory corruption and an infinite loop to cause a DDoS attack. The issue has since been remediated by the vendor in versions 1.3.0 and later.
Dr Kettle said: “Our continued commitment to identifying and addressing vulnerabilities within software means we can encourage vendors to implement best practices for cybersecurity and help keep users safe”.
The bug has been catalogued as ‘miniDLNA Remote Heap Corruption (CVE-2020-28926)’. You can read our Bug Disclosure Policy here.



